In this post we will look at how a Blockchain works, a technology that is trying to revolutionize the way in which we store and share information online. We will also build an example of a Blockchain, explore the different qualities it has and look at the types of Blockchain that exist today. Join us on this fascinating journey into the world of Blockchain technology!
What is the Blockchain?
The blockchain is a distributed database to which its participants have access. This database is distributed over a network in which participants can validate the data with cryptography, as if it were a large, unmodifiable, shared ledger.
One of the main differences between a blockchain and a centralized network is how the data is structured. The blockchain collects information in different packages, also known as blocks. These blocks have a certain capacity and, once they are filled, they are attached to the previous completed block, thus forming a data chain. This means that the data is ordered sequentially and temporally.
Another difference between a blockchain and a centralized network (where a single entity has control of all the data) is where it is run. While in a traditional centralized network there is a single entity in charge of execution, in a blockchain it runs on multiple computers around the world. Because of this, the blockchain has advantages such as greater privacy, decentralization and security. However, it also has a number of associated disadvantages, such as higher resource consumption.
Although blockchains are often associated with networks that store payment data, their utilities go far beyond that. We could have blockchains dedicated to storing medical data, logistical data or even voting tallies.
How does Blockchain work?
The main purpose of blockchain is to communicate important information between its participants. Moreover, we want to do this in a way that is secure and without the need to trust other users.
Let’s assume the following case. At Damavis’ next integration meeting, seven of its employees want to play the popular Monopoly game. However, after opening the box, they discover that an important element of the game, money, is missing. To solve this problem, Dani, one of the players, proposes that all the money transactions be written down on a sheet of paper in a notebook.
In this way, the game begins in the usual way. After a while of playing, the account book looks like this:
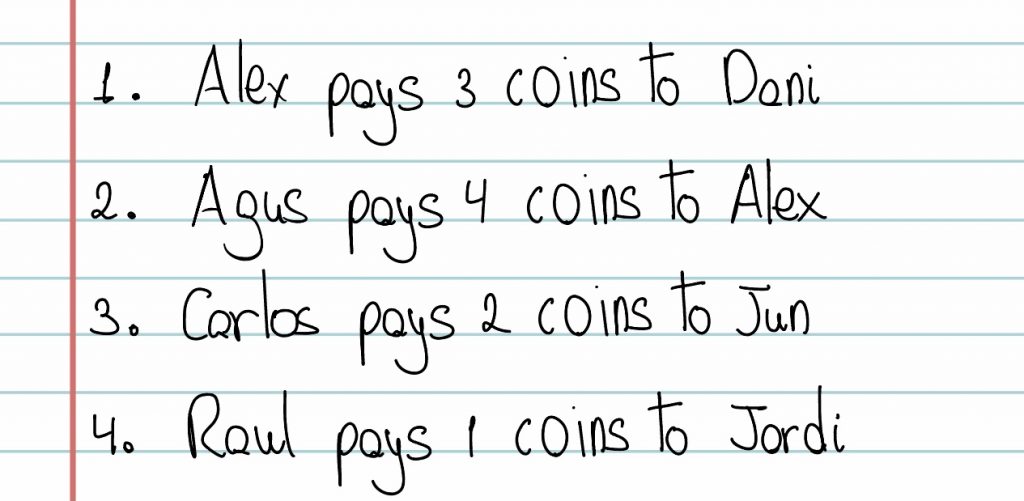
However, Alex, one of the players in the game, is determined to win at all costs, so he changes one of the operations as follows:

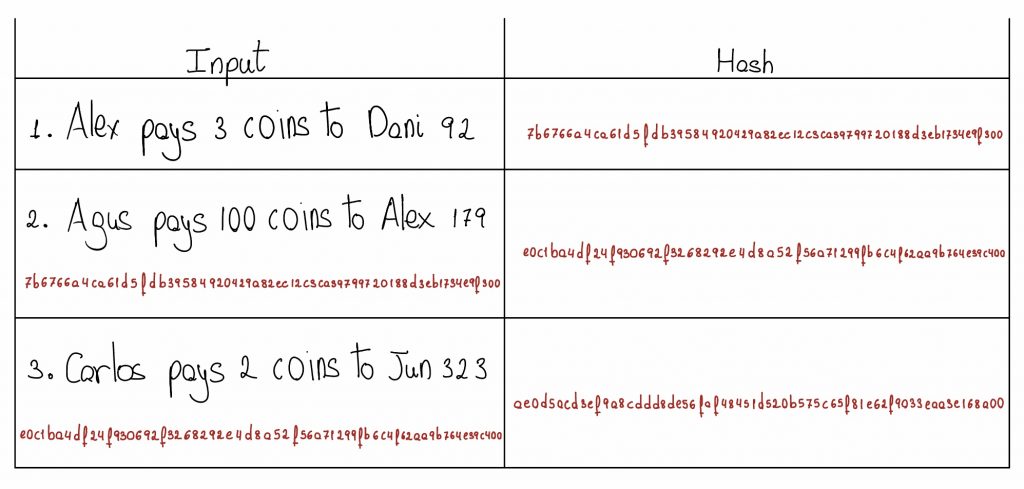
When it is Dani’s turn, he discovers the manipulation. To prevent future malicious attacks, he proposes to transform the operations using a hash function, which converts the text into a set of numbers and letters. This transformation will be added below the corresponding text string. In this way, the ledger would look like the following. (Note: Hashes are approximate):
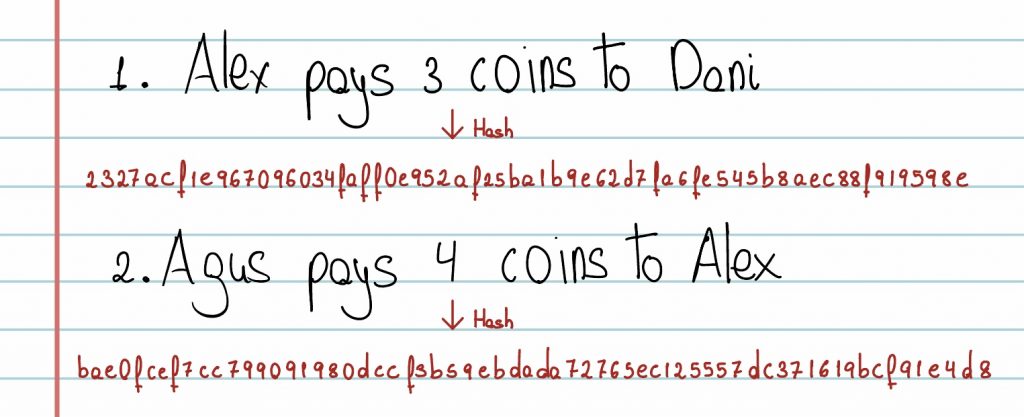
A small alteration to any character in the string would result in a completely different hash. So, players start adding each hash function after each string of text. For Alex, however, this is no problem at all. By changing the string again and calculating his new hash, he can get away with it again.
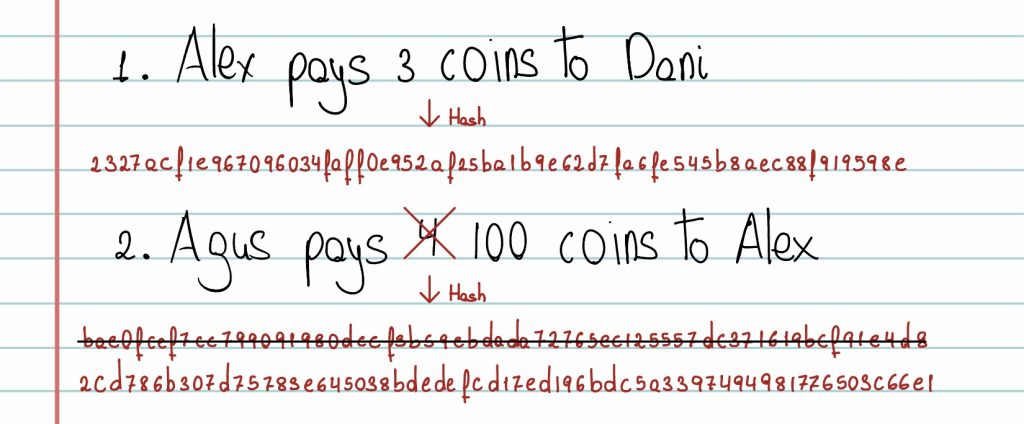
To make it even more complicated for the attacker, it is decided by consensus to add the hash of the previous transaction to each new entry. In this way, the transactions depend on each other, so if someone wants to change an entry in the middle of the chain, they must also alter the following entries.

However, Alex is still determined to cheat, so as soon as it is his turn, he quickly changes the transaction he is interested in and modifies the corresponding hashes.

Tired of the fact that one player is constantly altering the ledger, it is decided to complicate the calculation of each new entry. To do this, after each transaction, the players agree to add a number to the transaction. This number is known as a nonce and must comply with the hash function ending with two zeros (in general, the number of zeros is determined by the number of participants in the network; in this example, two zeros are used for illustrative purposes).
This system is cheat-proof, because if Alex wants to alter one of the entries in the ledger, he has to spend hours and hours calculating the nonce for each of the lines after the block he wants to modify.
Advantages of Blockchain technology
In the previous section we have seen how blockchain works on a small scale. In general, in blockchains with a large number of participants, other concepts come into play, such as miners, mining difficulty, nodes and other elements. However, in the example above we have already seen several of the desirable properties of this technology.
- Security: In general, blockchains provide a high degree of security against attacks or tampering attempts. This is because, in order to add a new block to the chain, it is necessary for the participants to reach a consensus. The blockchain would be at risk if more than 50% of the participants agreed to manipulate the network. This is known as a 51% attack.
- Transparency: network participants can see all transactions, so data is traceable.
- Decentralization: In the example above there was a single ledger where transactions were recorded. In general, blockchains have different computers that are responsible for validating each transaction, known as nodes. This decentralized architecture means that the network never collapses, so that even if one of the nodes disconnects from the network, the network is not at risk.
What is cryptocurrency mining?
Mining is the process by which miners add new blocks to a blockchain. It is also responsible for the creation of new cryptocurrencies. As mentioned above, in order to add a new block to the chain, it is necessary for the participants of the network to reach a consensus. For this, there are different protocols, among which the following stand out:
- Proof of Work (PoW): this is the most common in cryptocurrency mining, and is based on miners solving complex mathematical problems to validate transactions and add new blocks to the blockchain. In PoW, the miner who solves the mathematical problem receives a cryptocurrency reward.
- Proof of Stake (PoS): in this type of consensus proof, nodes that validate transactions are chosen based on the number of cryptocurrencies they hold, rather than on their processing power. The idea is that the more cryptocurrencies a user has, the more interested they are in the system working properly, and therefore the less likely they are to act maliciously.
Applications of Blockchain technology
One of the most interesting applications of blockchain technology is smart contracts. Smart contracts are computer programs that automatically execute the terms of a contract agreed between two or more parties on a blockchain. These contracts are self-executing, which means that they do not need the intervention of third parties, such as lawyers or notaries, to be executed.
Moreover, as they are based on blockchain technology, they are immutable, transparent and secure. This transparency allows the parties involved to check the status of the contract and its performance at any time.
Smart contracts can be used in a wide variety of fields, from finance and insurance to supply chain and intellectual property. In the game of Monopoly, Alex and Agus could reach an agreement for the sale and purchase of a property by paying a fixed amount each turn. When Alex had finished paying the agreed amount in full, the property would automatically become his property.
In short, smart contracts are a technological tool that allows the creation and execution of contracts in a more efficient, secure and transparent way.
Conclusion
Blockchain technology is a revolution that has changed the way we understand security and trust in the digital age. With its ability to offer transparency, immutability and decentralization, the blockchain has unlocked a new world of possibilities for applications in a variety of fields, from cryptocurrencies to smart contracts. In future blog posts we will cover other interesting aspects of this revolution, such as who created it, who uses it or how to program a smart contract. Stay tuned to stay up to date!
If you found this post useful, we encourage you to check out other articles in the Algorithms category on our blog. Don’t forget to share it with your contacts so that they can also read it and give their opinion. See you in networks!